Dominique West Creating your cloud security strategy with a DevSecOps Mindset
Reviews
Implementing Cloud Security using DEV ops Culture and Technology
Critical thinking and innovative strategies are essential to today's cloud security professionals. The recent upsurge in technological advancements is coupled with a surge in the complexity of security challenges. This article goes to the heart of how to harness the power of the cultural and technological shift in DEV ops for a comprehensive cloud security strategy.
About the Author: Dominique
Dominique, a cloud security professional, currently works as a Cloud Security consultant. She holds an undergraduate degree in Computer Information Systems and a Master’s degree in Cybersecurity. Dominique identifies as a factory-made security professional, having completed the traditional path into the field. When not navigating the worlds of cybersecurity and cloud security, she enjoys travelling, reading, and gaming as well as being an avid fan of BT S. Dominique is also the founder of Security in Color, a weekly cybersecurity podcast focusing on cybersecurity news and cloud security topics.
Busting Cloud Computing Myths
The cloud is commonly misunderstood, often assumed to be automatically secure or inherently unsafe. This spawns myths such as "the cloud is unsafe", "the cloud provider's security is sufficient", and "I need an entirely new team to manage cloud security". These misconceptions often stem from the lack of understanding about the cloud and its potential.
A crucial concept to understand when securing the cloud is the shared responsibility model. Shifting your security mindset from on-premise to cloud-based systems involves acknowledging that you, as the client, are responsible for security in the cloud, while the cloud service provider ensures security of the cloud.
Significance of Cloud Security Strategy
Cloud adoption is no longer a hypothetical consideration. Enterprises increasingly rely on public cloud, prompting major investments in hardware and software. As cloud maturation accelerates, so does the need to reevaluate how we approach cloud security.
Moving to the Cloud: Key Considerations
- Understand your organization's motivation for moving to the cloud - Are you shifting hardware or software, or meeting a regulatory requirement?
- Recognize that cloud adoption implies modifications across the entire organization, affecting operational, marketing, HR, and other channels.
Embracing the Shift-Left Culture in DEV ops
The concept of "Shift Left" emphasizes integrating security throughout the software development life cycle. This approach reduces the risk and cost of afterthought security measures, helping to address the unknowns that often plague cloud security.
Adopting a DEV Sec ops mindset involves integrating security at all stages, fostering collaboration amongst teams, leveraging automation, and nurturing 'security champions' within your teams. These strategies contribute significantly to the mitigation of security risks.
Conclusion
Migrating your organization’s security mindset from on-premise to cloud-centric is an evolution, not a one-off process. It requires a culture shift that stresses the importance of security, a deeper understanding of cloud security, and the integration of security measures throughout the development life cycle. By taking these strategic steps, organizations can anticipate, prevent, and mitigate security threats continuously, rather than reacting after incidents occur.
Organizations that neglect to transform their security teams jeopardize their counsel, labour, and financial investments into cloud security strategies. Start the conversation on the cultural and technological transition today. Achieving a Shift Left mindset will help maintain a resilient, secure, and cost-efficient cloud environment.
Video Transcription
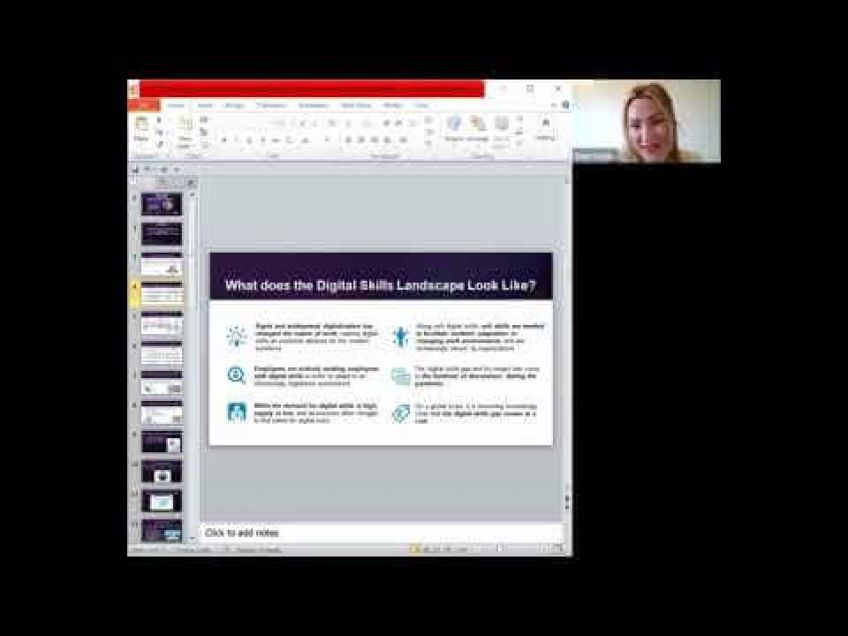
Well, hello and good afternoon. Thank you so much for tuning in to my session today.As you can see from the title, I will be discussing a topic I find super interesting and that is how adopting the cultural and technological shift seen in DEV ops can help cloud security professionals and it teams successfully implement a security strategy in the cloud. I currently work in cloud security. So I'm able to see these ups and downs firsthand and really take part in helping shift the security culture in a way that hasn't been done before. Now, there is a major concern with organizations across the board who agree that current security capabilities and strategies are lagging behind cloud adoption. And my goal today is to invoke critical thought when it comes to being a cloud security professional and how we can evolve as a community on our agenda. Today, I will be introducing myself a little bit with some fun facts. Um Then I will be demystifying cloud security by clearing up some myths. I will explain really quickly about the difference between traditional and on uh security in the cloud. And then we'll dive into why a cloud focused strategy is important.
Um I have some research and statistics for you and then we will deep dive into what's called the shift left mindset that scene from DEV ops to DEV set ups and what that really means for cloud security. And then we'll tie this up in a bow where I can give you some tidbits for you to take back to empower your own security teams. So some quick fun facts about me again. My name is Dominique. I'm currently a cloud security consultant for instant young, a multinational consultant firm. Um I call myself a like factory made security professional as I took the traditional route. Um in comparison to a lot of people today who are pivoting from different fields. Um I got my undergraduate degree in computer information systems um and then a graduate degree in cybersecurity. I am the founder of security and color, a weekly cybersecurity podcast covering cybersecurity news and cloud security topics. I love to travel. Um I'm an avid BT S fan and if I'm not binging or podcasting or watching all that stuff, I love to read and play video games. So let's dive into the talk today. We will begin our journey to building a cloud security strategy by first demystifying some common misconceptions that usually occur when it comes to cloud competing and cloud security.
So the five topics I present here, they're not all encompassing, but they are the most common and a lot of questions I've received in various situations when it comes to cloud computing. So myths such as uh you know, the cloud is unsafe or my cloud security uh provider automatically will keep me secure because, you know, they're Google or Microsoft. There's no way um I, I can have a breach there or, you know, my team, I need a new team in order to do this. The current team I have is not capable all those kinds of things and more that really happen. And, and that happens when there's not a full understanding of the cloud and it's pretty fair for a very long time. And still to this day, the cloud was seen as like this amorphous place. It's a place, you know, a technology without clear definition, there was no shape or standards, not a lot of frameworks for people to go off of, especially in the context of security and when used properly, the cloud is safer than a typical data center. Majority of the issues occur in the cloud, they come from poor security best practices and when you have complicated controls and rush technology programs that more often in the that leads to something happening.
And the shared responsibility model, which is a framework I will get into and visualize for you. Um In a couple of slides is a great starting point for all cloud security professionals and teams to really understand when things are confused about security and they don't know security of or in the cloud, many businesses they deploy into the cloud with the same on premise mindset thinking that's enough to cover both of their environments.
And unfortunately, the problem with the strategy is that many organizations don't understand their role and responsibility in the cloud or how compliance and securing data in the cloud actually works. And with the acceleration of the market ever increasing, we know how fast it is that everyone's trying to go to market or uh produce something out security gaps are continuing to happen. So just to give a better visual of the shared responsibility model, I just alluded to this model really shows the delineation of responsibility between a business and the cloud uh service provider. So customers meaning the business or you as a user, um your security teams, your business teams, whoever it is, that's in the cloud. You are responsible for security in a given cloud environment. So what this means to the customer is that you configure things like um your firewalls, you are the one responsible for protecting your customer data, things like P I IP H I, things that we don't want to get out there. You have to deal with application, security, identity and access management, uh things like encryption.
There's a lot of configuration that comes with being in the cloud that a lot of teams don't know off the bat, especially if you don't know which kind of deployment you're gonna go with and the CS P or the cloud service provider, they take care of security of the cloud. So they deal with making sure like things like regions um which you deploy into which like North American region, the Asian region, things like that. They make sure that those regions are durable available and secure for you the user to use. And they also deal with security of storage networking, you know, things that like at the edge, there's edge technology, you know, there's plenty of in depth white papers that I always recommend for people to go to as a starting point in order to really understand this uh shared responsibility model.
Now that we've clarified some misconceptions. Let's jump into understanding why knowing how to create a strategy as a security professional is important and why on premise one you have doesn't really apply here. The public cloud is no longer a what if for organizations cloud adoption is now pioneering literally everything. It's the next wave of technology evolution. 65% of enterprises are currently relying on public cloud. They're spending about 300 it's estimated to be spent about $354 billion within the next two years. And as we all know by now getting to the cloud is not a small task, it's a really major feat and it costs a lot of money. Research shows that for every $1 you spend in innovation, you will spend another seven on execution. And the reason for this really is because traditional data centers are not modernized for cloud adoption and it really forces a business to invest in new technology and to train their teams on how to operate these new systems. The impact of cloud adoption affects the entire organization, not just it and security teams anymore.
So what this means is that operation teams are involved, marketing is involved hr any team that will be a part of the cloud ecosystem or the cloud environment, they're all now part of that equation and all of your existing processes and controls should be a fundamental part of this shift.
And a really important question that I employ cloud security professionals as you're coming into it. Um And you're getting to, you know, learn your own career and you're trying to figure out how do I help a company migrate? You need to ask, well, what is my underlying motivation for moving to the cloud? You know, am I looking, is my business looking to do a major hardware shift? Are we doing a software shift? Is it caused by a new regulation like PC I GDPR, the California Protections Act, whatever that is the knowledge of that is really important to have. So you can begin a path of success to the cloud otherwise you'll end up wasting a lot of money. And you look like Dave Chappelle here, we want to make sure everyone is maximizing their money when moving to the cloud. So in cloud adoption, there are some stages that are pretty much understood uh uh uh during this journey, the names of which of each model may differ. There are some models that have four steps instead of five, there are some um that include even last a little bit more. But for, for the most part, they might be um called different um like get moving was also called kind of like migration. So there's a different uh names for each one. But I wanted to highlight an overview of these steps for two reasons. One to introduce what the cloud journey looks like for those of you who might not be familiar. But two.
And really my main reason for you is to understand the current state of where the security teams are brought into the pipeline of migrating to the cloud and why security challenges continue to occur. It is here after the migration stage and before the opti optimization stage, the organizations really start to assess their security posture and then they start to ask questions like, you know, is the application I'm deploying? Is it secure? Have we taken care of all the vulnerabilities?
Do we have the right tools in place to monitor? You know how I done my due diligence? And it really is here in the beginning um of gap analysis before you even get started deploying anything. When you just start thinking about, you're going to the cloud. It is here that these questions should be asked and your security team should be brought in. And this continuous mindset of really bolting security on into the cloud is why security challenges continue to be faced. According to a cloud security survey by IC C square last year, 93% of surveyed security professionals say they are moderately to extremely concerned about cloud security. And this uptick is um this is an uptick from 90% seen just in 2018. And it really speaks to the increased threat landscape that security professionals and organizations are experiencing with cloud adoption. And it's really just underscores that if there's such a complexity, you know, being brought to organizations, there really is a sh a need to have a a shift in strategy technology and culture um in cloud security in order to mitigate these things. And as cloud uh maturation increases, businesses are really beginning to recognize the significant impact that management decisions, you know, about cloud security strategies and implementations can have. And the design of cloud native features are way different than what you see on premise.
And not having a strategy is increasingly opening organizations to more risk than they bargained for and continue to roll out. We just again, waste money like I said before and really just continue to have the challenges here. So let's dive into what it means to really shift left and what shift left is like this cultural mindset that I really want to allude to in the development pipeline. And how applying that culture to cloud security can help solve a lot of these challenges that I alluded to before and some that you might have encountered in the first place. So if you are a security professional or part of a developer team, or you might already be familiar with the term shift left or dede s terminology. Um And if not a shift left simply means that security. So security teams or security as a pro is built into this pipeline and designed early in the stage instead of what it has, where it has historically been as I alluded to before with the bolt on security is that it comes really later on when it's a little bit too late and when it is far too late and little time to get to the deployment stage, people are left scrambling about what should I do.
So the shift left mindset is usually in reference to the software development life cycle. The goal is to really increase, you know, quality, reduce the amount of time required for testing and most importantly, really mitigate the security risk um to make sure things are less expensive.
Now, there are a ton of ways in which dete optics explain in pictures, but they all tell really the same story. It's really merging development operations and security together in order to promote fast development of a secure code base. So as I stated earlier in highlighting security challenges faced in the cloud, an overwhelming number of businesses are in a very stage of cloud adoption. Thankfully, with this dese ups methodology, a lot of which you can see here um if implemented correctly can really answer a lot of these unknown questions and break the regular trend of having security as a separate process. Many organizations from start ups to 14 500 have still have this built on security mentality and without breaking this really counterproductive norm that plays our industry. For so long as security professionals, we will always be playing catch up during this technological evolution and it teams will always be in a reactive state rather than a proactive state, which is really what we want to get to de se ops, calls for security integration at all stages.
And the following are six factors in DEV se ops that can really ha um aid in successfully implementing security in a cloud environment. And this really acts like building blocks to creating a strategy in the cloud by embracing public cloud and shifting left with DEV ops and security organizations can see significant benefits, things like cost savings, risk reduction. And when done successfully, businesses can tangibly see rapid acceleration in the way they're able to really remediate vulnerabilities and significantly increase their security at the same time. Now de IOPS only works if organizations are willing to give their teams the resources and tools to be successful.
So things like security teams needing to adapt to other teams that's really important. And I know a little bit blasphemous as security professionals because we always think, hey, see that I, you know, my way or the highway kind of mentality, um which is something, you know, that we should definitely improve on in order to collaborate with other teams, then we have things like automation, that's something that's up and coming.
Automation really is the, the, the uh key to being successful. Um because it's the human problem, you know, we have errors, we're prone to errors, we get thousands, millions of logs and signals every day. Automation really helps with that. We wanna make sure that we're training our teams and empowering our current security teams and that we wanna make sure to have a, a great, like a security champion, someone who can um be a part of another team with your security team and really talk and collaborate and let each other understand.
Well, here's my blockers, here's my barriers. Here's why I'm doing things that I'm doing. So some key takeaways from this presentation, um DEV Sec ops. I know this is a really, really quick highlight overview, but I just wanted the, I really, what was important to me is get the conversation started about the cultural shift that's happening in cloud security and how DEV ops can play a part into that. It's really about integrating teams, pooling resources together, leveraging this, we already have and really understanding that we all have a common goal. Um And we have common perspectives. So if you're not transforming your current security teams, you're really losing out.
If you're holding on to your existing security capabilities and mindset in the cloud, more than likely something's gonna happen with your team. The shift to de SE S is more than technology. It's really about a cultural shift. It's really about bringing teams together and really understanding how can we make sure that we are um leveraging our best resources and skills and attacking the threat landscape as best as possible. You're going to have some bumps along the way, but you know, you're gonna have to iterate a lot. It might be annoying, but trust me, it is well worth it when it's done, right? And you see how much you can take advantage of the cloud and really change your culture and your business. So thank you so much for that. I know that was really, really, really quickly. Oh, that's not a good scheme. Um You can find me on social media at Dummy Boo. My website is called Security and color.com. That's where I have a longer version of this talk. If you're really interested, you can find me on linkedin or social media. I'm really passionate about this subject. If you want to talk to about me, please follow me or go ahead and please contact me. Um You can see the longer version and I hope you guys enjoy the rest of your sessions. Do I have a lot of time left to like, answer one question?
Um Thank you so much. OK. Uh I will put it in the chat for you and I think you can click my profile and get stuff, but I'm not too sure. I don't for them to say. Um and then uh the podcast is on, um, every platform is on Apple Podcast, Google Podcast, Spotify, all that kind of good stuff. That's where I talk a lot about um, cybersecurity news that's happening every day. I give you the top five cybersecurity. And then if you're interested in cloud security, I break down a lot of topics every Thursday as well. Thank you so much, everybody.




No comments so far – be the first to share your thoughts!